Every successful project, big or small, starts with a clear understanding of what needs to be done. Without that foundational clarity, even the most promising initiatives can quickly descend into confusion, missed deadlines, and budget overruns. In the fast-paced world of cybersecurity, where precision and compliance are paramount, having a well-defined project roadmap isn’t just helpful, it’s absolutely essential for safeguarding digital assets and ensuring operational continuity.
This is precisely where a robust security scope of work template becomes an invaluable asset for any organization or consultant. It acts as a detailed blueprint, outlining every facet of a security project from its initial objectives to the final deliverables. By meticulously documenting expectations, responsibilities, and timelines, it helps prevent misunderstandings, streamline communication, and ultimately drives projects to a successful and secure conclusion.
Throughout this article, we will delve into the critical elements that make up an effective security SOW, explore why it is so crucial for navigating complex security landscapes, and provide practical advice on how to tailor and implement one for your specific needs. Prepare to transform your approach to managing security projects.
Why a Robust Security SOW is Your Project’s Best Friend
In the realm of cybersecurity, ambiguity can be your worst enemy. A well-crafted Scope of Work (SOW) serves as the bedrock for any security initiative, whether you are implementing new defenses, conducting a penetration test, or auditing compliance frameworks. It defines the boundaries of the engagement, ensuring that everyone involved – from the client to the project team – shares a common understanding of the goals, methods, and expected outcomes. Without this document, projects are susceptible to “scope creep,” where additional tasks are added without proper planning, leading to delays and increased costs.
Think of your security SOW as a meticulously drawn map for a critical mission. It specifies the starting point, the destination, and the exact route to take, alongside any potential obstacles and how to navigate them. This level of detail not only prevents misunderstandings but also acts as a vital reference point throughout the project lifecycle, allowing all stakeholders to track progress and verify that the work remains aligned with the original objectives. It translates high-level security aspirations into actionable, measurable steps.
Key Components to Include
To be truly effective, a security SOW needs to be comprehensive and leave no room for guesswork. Here are the essential elements you should always incorporate:
- Project Overview and Executive Summary: A concise introduction to the project, its primary objectives, and the desired business outcomes.
- Project Scope: Clearly delineate what is included in the project and, just as importantly, what is explicitly out of scope. This prevents future disputes.
- Deliverables: List all tangible outputs expected, such as security audit reports, vulnerability assessments, implementation plans, or training materials.
- Milestones and Timeline: Break the project into phases with specific deadlines and key progress points.
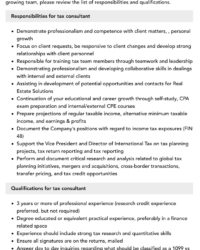
- Roles and Responsibilities: Define who is accountable for what, for both the client and the service provider.
- Payment Schedule: Outline the financial terms, including payment amounts, dates, and any conditions for payment.
- Acceptance Criteria: Establish the standards by which deliverables will be judged as complete and satisfactory.
- Assumptions and Constraints: Document any factors assumed to be true for the project to proceed and any known limitations.
- Legal and Compliance Considerations: Address any relevant regulations, industry standards, or legal frameworks that must be adhered to.
Each of these components plays a crucial role in building a comprehensive and clear SOW. The clearer and more detailed each section is, the less likely you are to encounter issues down the line. It demands a thorough understanding of the project’s intricacies before any work even begins.
Avoiding Scope Creep and Misunderstandings
One of the greatest benefits of a detailed security SOW is its power to mitigate scope creep. When the boundaries of a project are vaguely defined, it is incredibly easy for additional requests or tasks to be subtly added, expanding the workload without corresponding adjustments to resources or timelines. The SOW serves as an official reference point, allowing project managers to politely but firmly refer back to the agreed-upon terms when new requests arise, facilitating proper change management processes instead of uncontrolled expansion. It keeps everyone accountable to the original agreement.
Moreover, the SOW is an invaluable tool for preventing general misunderstandings. Different parties might interpret verbal agreements or even high-level discussions in diverse ways. By putting everything in writing, with specific details and clear language, you ensure that there is one unified document that represents the collective agreement. This minimizes confusion, reduces conflict, and fosters a more collaborative and productive project environment. It aligns expectations from day one.
Practical Tips for Customizing Your Security SOW Template
While a robust security scope of work template provides an excellent foundation, it is crucial to remember that no two security projects are exactly alike. True effectiveness comes from customizing that template to perfectly match the unique nuances, objectives, and environment of each specific engagement. A boilerplate SOW, no matter how well-designed, will likely fall short if it isn’t thoughtfully adapted to the client’s particular security posture, technological infrastructure, and regulatory requirements.
The key to successful customization lies in a thorough discovery phase. Before you even start populating your template, invest time in understanding the client’s pain points, their ultimate goals, and any specific constraints they might have. Are they looking for a comprehensive vulnerability assessment, a focused penetration test on a single application, or a full-scale security architecture review? The depth and breadth of your SOW will drastically change based on these initial insights. Engage in detailed conversations and ask probing questions to uncover all the critical information.
Here are some practical tips to guide you in tailoring your template for maximum impact:
- Conduct a thorough requirements gathering session with all key stakeholders to ensure every expectation is captured.
- Tailor the language to the specific industry and technical context, using terms that are clear and understandable to both technical and non-technical audiences involved.
- Be flexible with the structure, adding or removing sections as needed to perfectly fit the project’s complexity and scope.
- Emphasize potential risks and mitigation strategies relevant to the project’s unique challenges.
- Include specific metrics for success that are directly applicable to the project’s objectives, making outcomes measurable.
By diligently applying these customization strategies, your security SOW template transcends being just a generic document. It transforms into a powerful, project-specific contract that not only outlines the work but also fosters transparency, builds trust, and paves the way for a successful security outcome, ensuring all parties are aligned and committed to the same vision.
The effort invested in crafting a meticulous security SOW pays dividends throughout the entire project lifecycle. It not only sets clear expectations at the outset but also serves as a vital compass, guiding the team, managing stakeholder expectations, and minimizing the potential for costly misunderstandings or uncontrolled scope expansions. A well-defined scope of work is not merely administrative overhead; it is a strategic asset that underpins the success and integrity of every cybersecurity initiative, providing the clarity and direction needed to navigate complex digital landscapes confidently and securely.